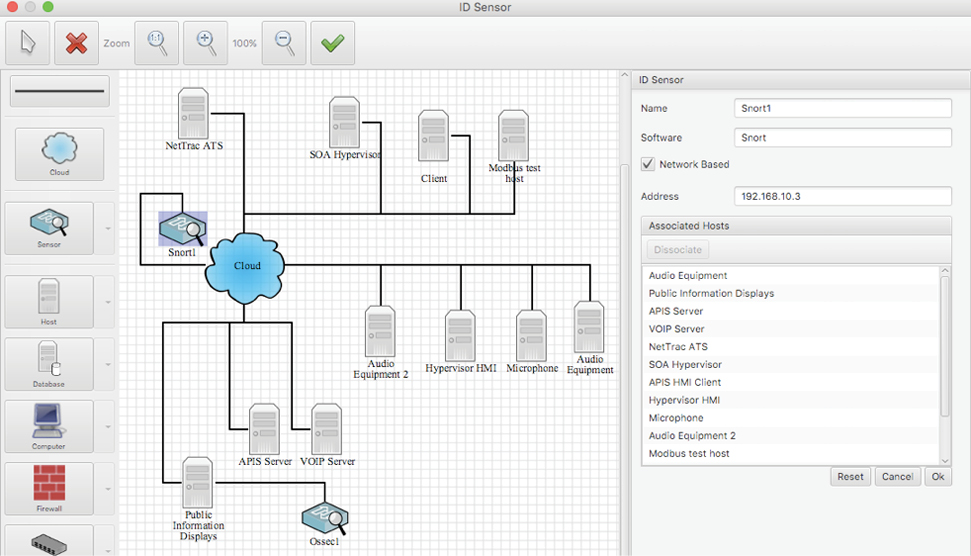
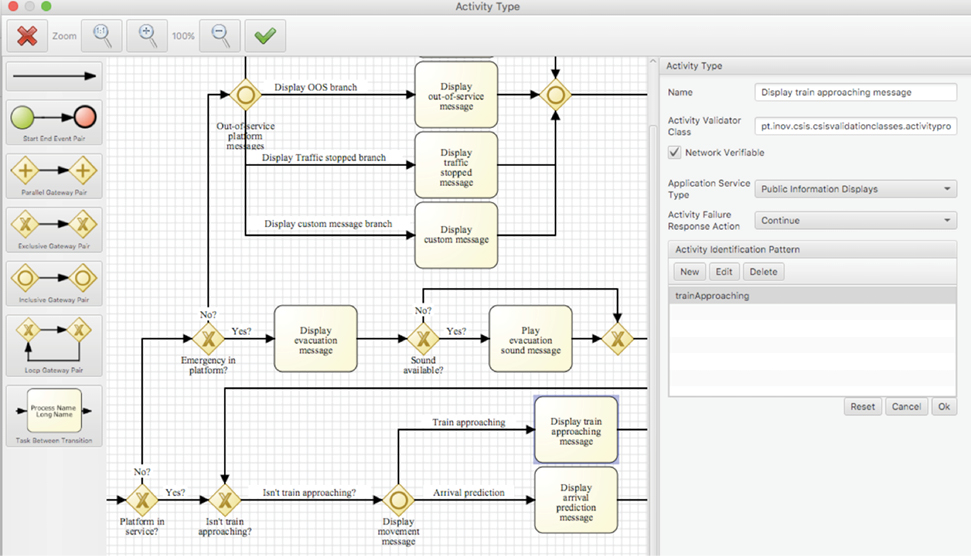
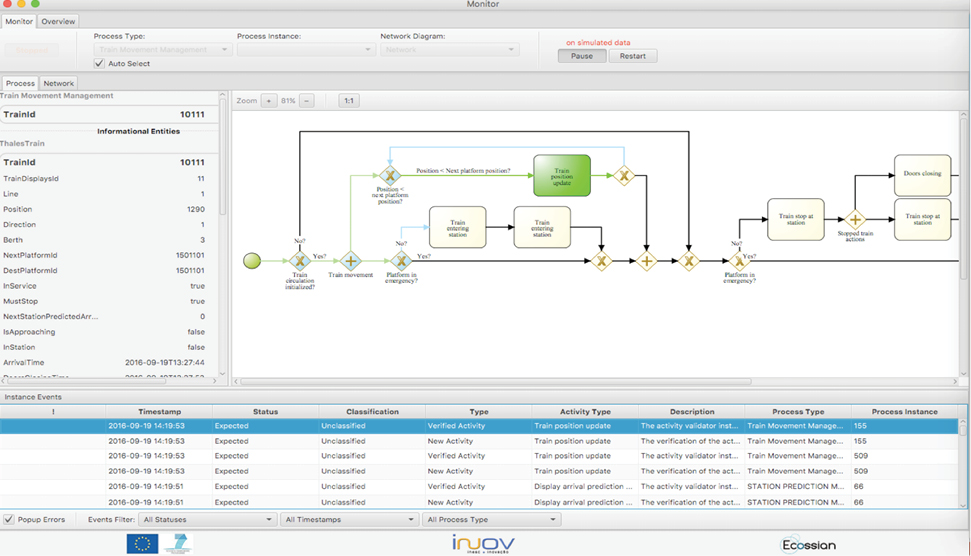
BP-IDS can detect known and still unknown types of cyber attacks, by how they affect operations.
PROTECT YOUR ORGANISATION
FROM CYBER ATTACKS AGAINST
CORE ASSETS
The extensive usage of Information and Communication Technology (ICT), such as: laptops, mobile phones, industrial control systems, access control systems, etc., as well as the usage of complex and safety critical automation and legacy systems, means that organisations are now more vulnerable to attacks from both outside and inside threat actors.
WHAT IT IS
Fight intrusions and inside threats, while having real-time quality monitoring of business processes

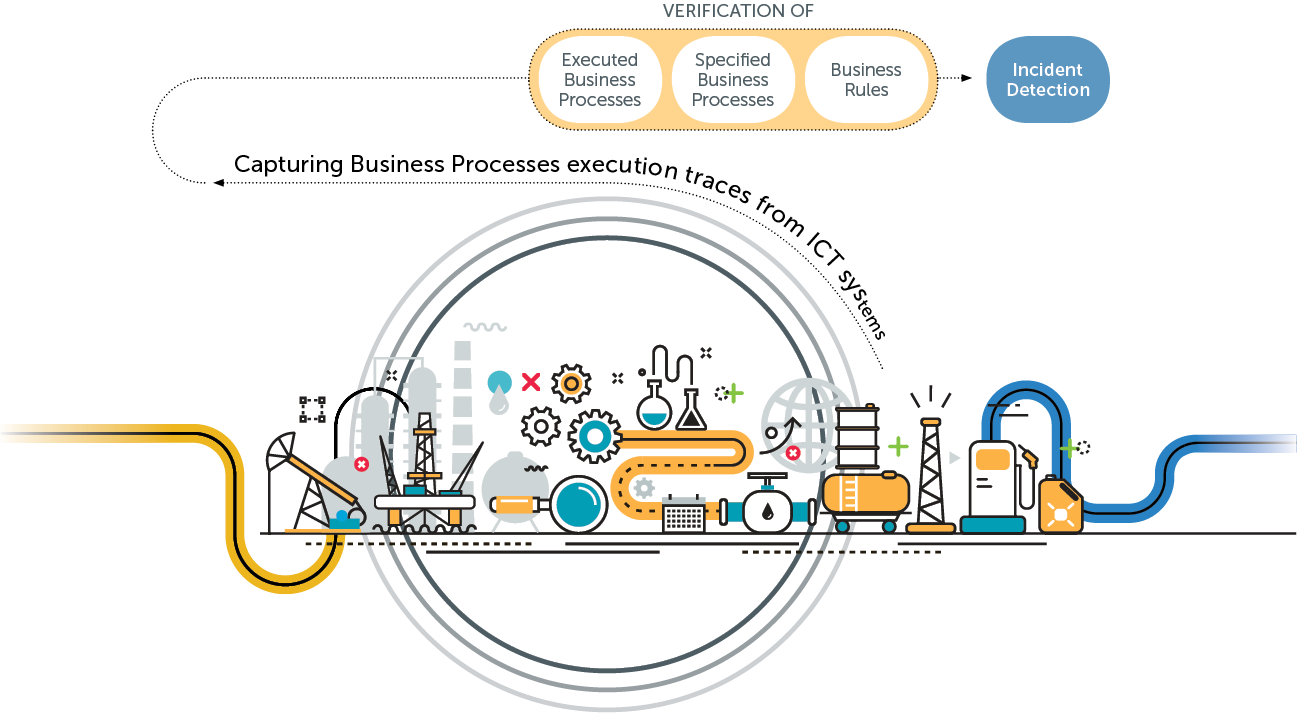
Aimed at critical Infrastructures, such as energy networks, transportation operators and industrial facilities, INOV developed BP-IDS which collects traces of business process execution through a set of passive sensors installed on the organisation’s ICT infrastructure, and compares it in real-time with the business process BPMN specification.
Whenever there is a violation of a business process specification, the organisation’s quality, efficiency, safety or security have been compromised.
In these situations BP-IDS triggers an incident alert to protect the whole system, from advanced cyber attacks, social engineering and inside threats, as well as quality violations and exceptions.
When compared with other existing IDS solutions, BP-IDS is characterized by a low rate of false positives and the ability to detect unknown types of attacks.
EU Patent number EP2911362A2
AIMED AT
Critical Infrastructures and Industry such as:
Electric and Gas Power Stations / Railroad and Transportation Networks / Industrial Facilities




FEATURES
INCIDENT ALERT TRIGGER
Whenever there is a violation of a business process specification (such as for example, a set of actions executed out of the order by which they should be executed), BP-IDS triggers an incident alert which may be caused by:
INTRUSION/CYBER ATTACK – BP-IDS can detect known and unknown types of cyber attacks on critical systems and processes, allowing fast and effective response.
SOCIAL ENGINEERING AND INSIDE THREAT – Unlike most available tools, BP-IDS can detect an attack against the human element, by detecting illicit actions from insiders.
QUALITY VIOLATION – By measuring how and in what time business processes are executed, it allows BP-IDS to provide valuable information for real-time quality control.
HIGH-LEVEL INTEGRATED OVERVIEW
BP-IDS seamlessly provides complementary views of how an organisation’s business processes are being executed and what assets may be involved in a given incident. Besides a high-level dashboard, that allows tracking the state and status of organisation’s critical business processes, BP-IDS also provides:
BUSINESS PROCESS DETAILED VIEW – This feature allows following in real-time what is the status of each business process and monitor its key parameters. Whenever an incident is detected, BP-IDS presents what went wrong in the business process, with the information necessary for understanding the impact and probable causes of the incident.
INCIDENT RECORDING AND HANDLING – Each incident is recorded on BP-IDS together with incident handling history.
NETWORK VIEW – Allowing to identify which ICT and/or control systems are involved in each activity or incident.
BP-IDS integrates information from existing Intrusion Detection Systems (IDS), allowing to enrich its business process anomaly detection capability with specific ICT IDS information, also providing the understanding of the impact on the business process of a cyber attack against a given system.
Through a process-by-process approach BP-IDS can deliver an extremely low false positive rate, compared with existing anomaly detection systems.
ADVANTAGES
Support Systems: Business support services run in an infrastructure of networked equipment and monitored by host and network sensors.
BP-IDS – System architecture
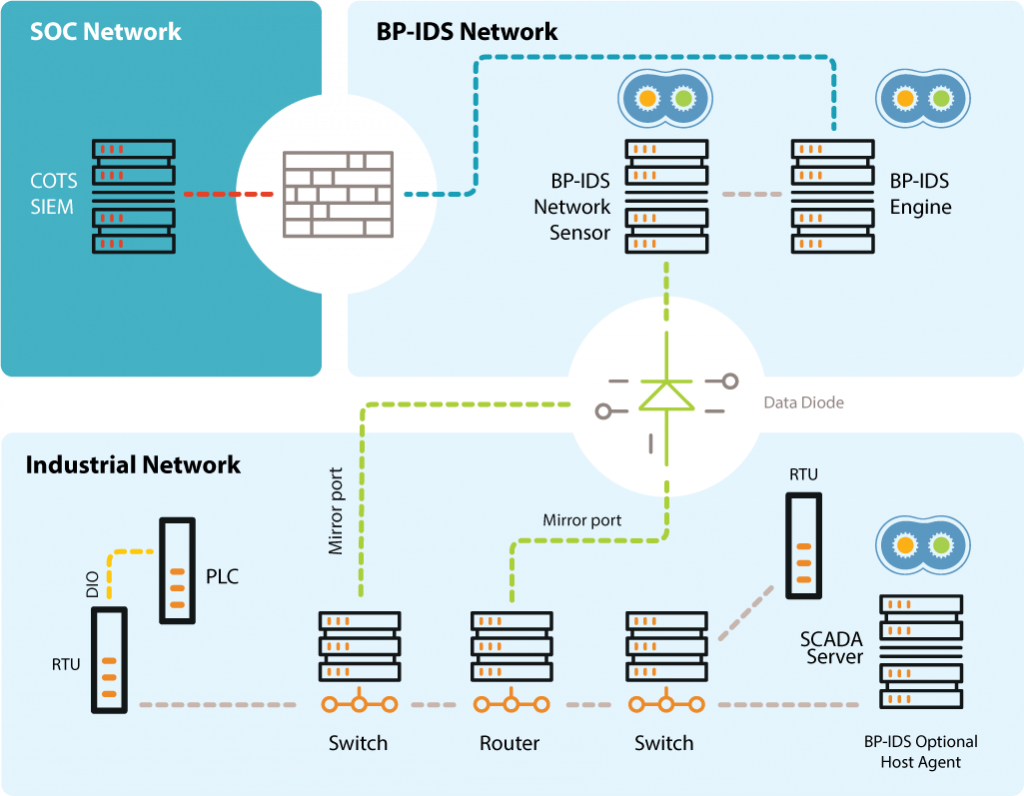
Specification of critical business processes, and how the IT systems interact during the process establish the baseline.
– Business processes are specified using a graphical representation (BPMN).
Information from network based and host based sensors that monitor existing systems, identify how the business process is being executed in real-time (current state).
Cross checking the system’s current state against the business process specification will allow detection if a given process is being violated.
Easily deployable on existing infrastructures in a non-intrusive way.
DEMOS AT
EU FP7 ECOSSIAN project

In the EU FP7 ECOSSIAN project, BP-IDS was tested, deployed and demonstrated in realistic setups, at an Energy Provider in Ireland and at a Railway Infrastructure Operator in Portugal. In these public events BP-IDS demonstrated the capacity to promptly detect man-in-the middle attacks in SCADA systems which covertly tried to manipulate the systems that control gas pressure and electric power distribution.
About us
 INOV positions itself in the market as the biggest national technological infrastructure in the field of the Information Technology, Electronics and Communications, as a successor of great assets arisen from extensive knowledge and experience implicitly provided by the maternal environment INESC. INOV officially started its activities on January 1, 2001, as a private nonprofit association.
INOV positions itself in the market as the biggest national technological infrastructure in the field of the Information Technology, Electronics and Communications, as a successor of great assets arisen from extensive knowledge and experience implicitly provided by the maternal environment INESC. INOV officially started its activities on January 1, 2001, as a private nonprofit association.
INOV provides an agile and flexible organisation, oriented to creating technological skills and establishing cooperation links with various economic entities (universities, industries, companies and Telecommunications Operators). For this purpose INOV intends to act as an intermediary between the University and the Industry, basing on the dedicated cooperation with the University in order to provide sustained, consistent and innovative solutions addressing the problems and challenges faced by our Partners.
For further information please send us a contact request